How-to Investigate Active Directory Logon Mischief
The Windows domain feature for locking accounts can be a helpful feature against malicious attempts to guess a password via brute force.
The version of netlogon.dll that has tracing included is installed by default on all currently supported versions of Windows. To enable debug logging, set the debug flag that you want by using nltest.exe, the registry, or Group Policy.
Group Policy
You will have to adjust a few policy settings to get the DCs to audit logon events. This are usually set correctly, but it can be worth a check of the environment to make sure the DCs are get the proper audit settings.
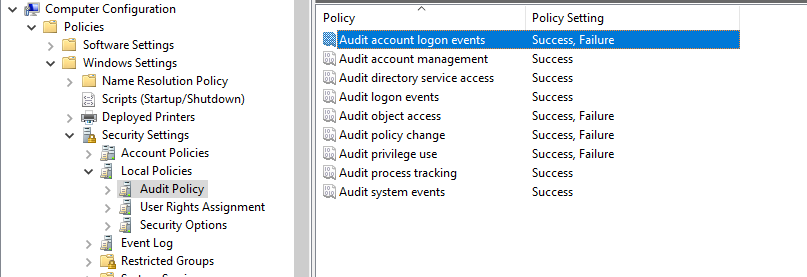
Audit account logon events for domain accounts and Audit logon events for logons to the computer.
Events
The Event IDs we are most concerned with are under the Windows Logs > Security section of Event Viewer.
- 4624
- 4776
If the auditing of Events on Domain Controllers doesn’t reveal the whole story, you can enable debug tracing in the NETLOGON service.
Enable Trace Logging in NETLOGON
If you try audit account logon but the workstation field keeps turning up empty you can enable trace logging on the DC trace debug logs output to C:\Windows\debug\netlogon.log
The log file netlogon.log can grow to 20MB and will be rotated out for a new log file.
To enable and disable trace logging in netlogon service, use the following nltest.exe commands respectively.
nltest.exe /dbflag:2080ffff
nltest.exe /dbflag:0
The following will be written to netlogon.log when you set the flags.
[MISC] [5584] DbFlag is set to 2080ffff
You will find entries these in the netlogon.log file.
[LOGON] [884] X: SamLogon: Transitive Network logon of (null)\ADMIN from (via X) Entered
[LOGON] [884] X: SamLogon: Transitive Network logon of (null)\ADMIN from (via X) Returns 0xC0000064
More information
Enabling Debug Logging for the NETLOGON Service
Increase Service Logging
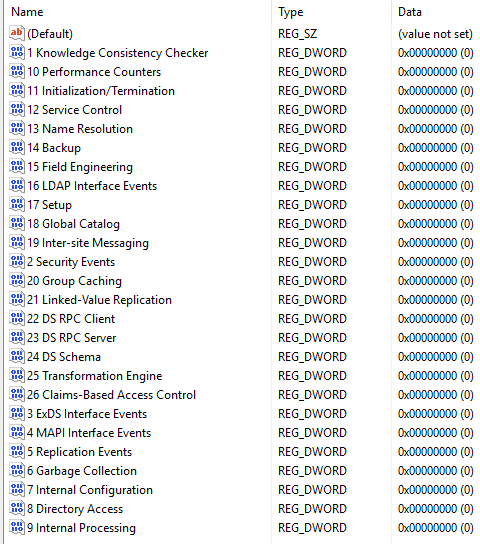
At times it can be help to increase the logging for a given component, like LDAP Interface Events. You have to do this using regedit, under the following key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Diagnostics
Conclusion
It can be hard to find logon activity in a Windows environment. But, if you have the right policies enabled and know which debug settings to turn when you need to troubleshoot activity, you will be that much further ahead.